Aws Security White Paper 2017

Amazon web services amazon web services.
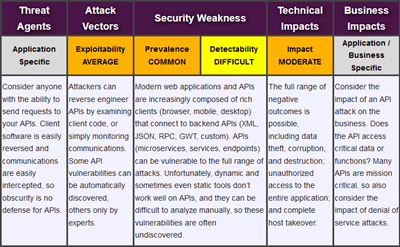
Aws security white paper 2017. The number 9 item in this list the auditing security checklist has been replaced by a cloud audit academy course. This documentation assists customers in understanding the controls in place relevant to the aws services they use and how those controls have been validated. Aws recently released the aws security incident response whitepaper to help you understand the fundamentals of responding to security incidents within your cloud environment. The whitepaper reviews how to prepare your organization for detecting and responding to security incidents explores the controls and capabilities at your disposal.
Aws provides a wide range of information regarding its it control environment to customers through white papers reports certifications and other third party attestations. The following list includes the ten most downloaded aws security and compliance documents in 2017. These are basically the same security tasks that you re used to performing no matter where your servers are located. As systems are built on top of aws cloud infrastructure compliance responsibilities will be shared.
With aws you control where your data is stored who can access it and what resources your organization is consuming at any given moment. Using this list you can learn about what other aws customers found most interesting about security and. This paper provides in depth best practice guidance for architecting secure workloads on aws. Amazon web services overview of security processes page 9 aws compliance program amazon web services compliance enables customers to understand the robust controls in place at aws to maintain security and data protection in the cloud.
Amazon web services security pillar 2 security the security pillar describes how to take advantage of cloud technologies to protect data systems and assets in a way that can improve your security posture. Each section has links to aws documentation that provides more detail on the best practice or capability. The paper is intended for it decision makers and security engineers who are familiar with the basic concepts of networking security and aws. Aws recently released the aws security incident response whitepaper to help you understand the fundamentals of responding to security incidents within your cloud environment.




%2C445%2C291%2C400%2C400%2Carial%2C12%2C4%2C0%2C0%2C5_SCLZZZZZZZ_.jpg)